“how to secure business data during digital transformations”
Related Articles
- “cybersecurity Compliance Standards For Healthcare In 2025”
- “data Breach Insurance Requirements For Businesses”
- “how To Secure IoT Devices In Corporate Networks”
- “how AI Is Reshaping Data Security Strategies In 2025”
- “data Security Trends For Financial Institutions In 2025”
Introduction
Welcome to our in-depth look at “how to secure business data during digital transformations”
The very concept of a "perimeter" is blurred as data resides across various locations – on-premises servers, cloud platforms, employee devices, and even third-party applications. The "secret" here lies in adopting a Zero Trust Architecture (ZTA). ZTA assumes no implicit trust, verifying every user and device attempting to access resources, regardless of their location. This involves:
.png?width=1758u0026height=1318u0026name=digital%20transformation%20benefits%20(3).png)
- Microsegmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the attacker’s access is restricted to that segment only.
- Multi-Factor Authentication (MFA): Implement MFA for all users and devices, adding an extra layer of security beyond passwords. This can include biometric authentication, one-time codes, or security keys.
- Device Management: Enforce strict device security policies, including encryption, regular software updates, and remote wipe capabilities for lost or stolen devices. Utilize Mobile Device Management (MDM) and Endpoint Detection and Response (EDR) solutions to monitor and control access.
- Continuous Monitoring and Threat Detection: Implement robust security information and event management (SIEM) systems to monitor network activity, identify anomalies, and detect potential threats in real-time. This allows for quicker response times and minimizes damage.
2. Data Loss Prevention (DLP) – The Unsung Hero
Data loss prevention is often underestimated, but it’s a crucial component of a comprehensive security strategy. DLP solutions monitor data movement within and outside your organization, preventing sensitive information from leaving unauthorized channels. The "secret" is to go beyond basic email and web filtering:
- Contextual Data Loss Prevention: DLP should consider the context of data transfer. For example, a document containing sensitive customer information might be acceptable to share internally, but not externally. Sophisticated DLP solutions analyze the content and context of data to determine appropriate actions.
- Data Classification and Tagging: Implement a robust data classification scheme to identify and categorize sensitive data based on its confidentiality level. This allows for granular control and tailored security measures. Tagging data allows for easier tracking and monitoring.
- Integration with Other Security Tools: DLP should integrate seamlessly with other security tools like SIEM, firewalls, and access control systems to create a unified security posture.
3. Cloud Security: Mastering the Hybrid Landscape
Many digital transformations involve migrating to the cloud, either partially or fully. This presents both opportunities and challenges. The "secret" to cloud security lies in a multi-pronged approach:
- Shared Responsibility Model: Understand the shared responsibility model between your organization and the cloud provider. While the provider is responsible for the underlying infrastructure, you retain responsibility for securing your data and applications running on that infrastructure.
- Cloud Security Posture Management (CSPM): Utilize CSPM tools to continuously assess your cloud environment’s security configuration, identify vulnerabilities, and ensure compliance with security best practices.
- Cloud Access Security Broker (CASB): CASBs provide visibility and control over cloud applications and data, enforcing security policies and preventing unauthorized access.
- Encryption at Rest and in Transit: Encrypt all data stored in the cloud and during transmission to protect it from unauthorized access, even if a breach occurs.
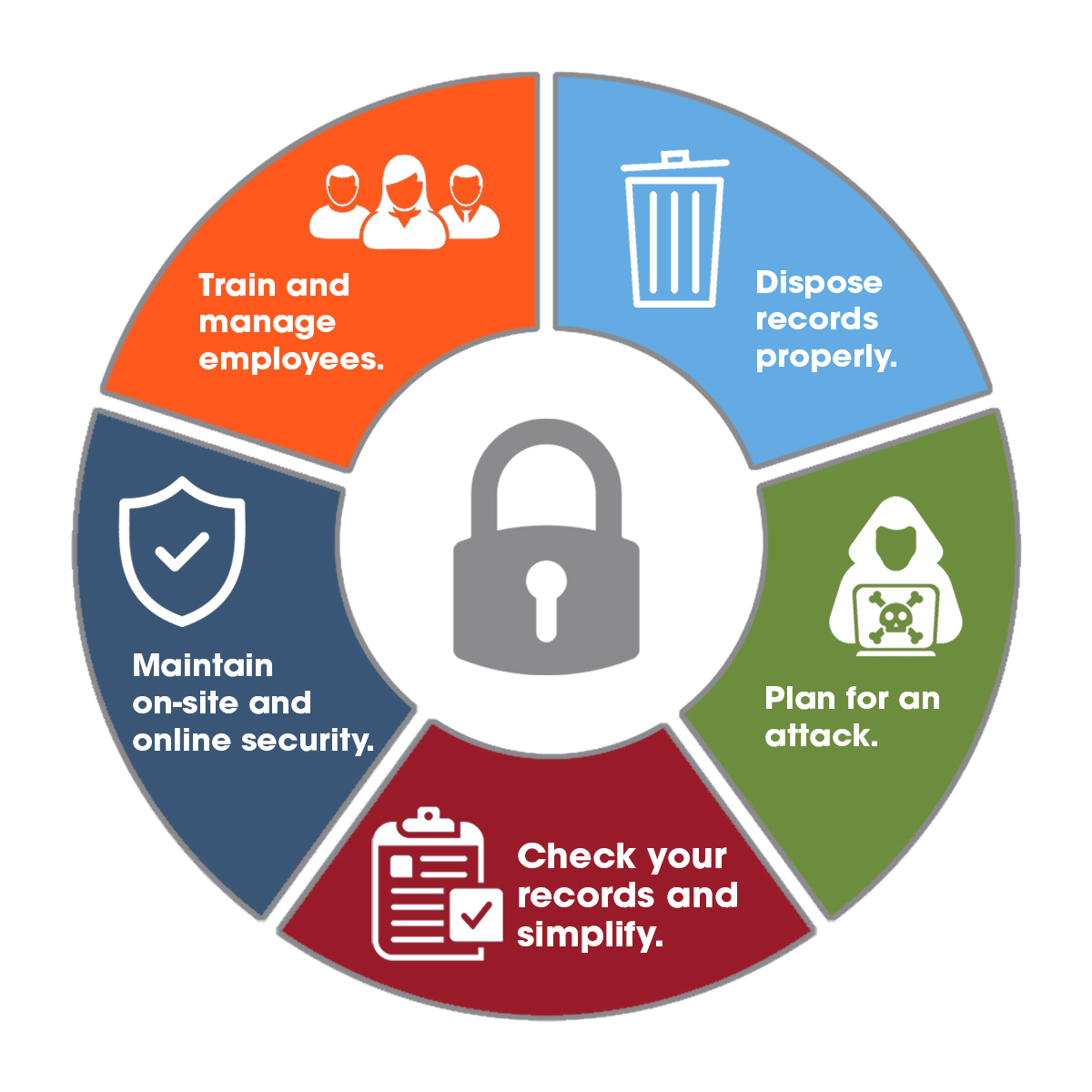
4. The Human Element: Security Awareness Training
Employees are often the weakest link in the security chain. Phishing attacks, social engineering, and accidental data leaks can have devastating consequences. The "secret" lies in investing in comprehensive security awareness training:
- Regular Training: Conduct regular security awareness training sessions to educate employees about various threats, best practices, and the importance of reporting suspicious activity.
- Simulated Phishing Attacks: Conduct simulated phishing attacks to test employee awareness and identify vulnerabilities. This provides valuable insights into your organization’s security posture.
- Incident Response Plan: Develop and regularly test an incident response plan to effectively handle security breaches and minimize their impact. This includes clear communication protocols and escalation procedures.
5. Vendor Risk Management: Protecting Your Extended Enterprise
Digital transformations often involve working with third-party vendors, who may have access to your sensitive data. The "secret" to managing this risk lies in thorough due diligence and ongoing monitoring:
- Vendor Risk Assessments: Conduct thorough risk assessments of all vendors before engaging them, evaluating their security practices and controls.
- Contractual Agreements: Include strong security clauses in your contracts with vendors, outlining their responsibilities and liabilities regarding data security.
- Continuous Monitoring: Regularly monitor the security performance of your vendors to ensure they maintain adequate security controls.
6. Data Backup and Recovery: The Ultimate Safety Net
Data loss can be catastrophic, disrupting operations and causing significant financial damage. The "secret" is to implement a robust backup and recovery strategy:
- 3-2-1 Backup Rule: Follow the 3-2-1 backup rule: maintain three copies of your data, on two different media types, with one copy stored offsite.
- Regular Testing: Regularly test your backup and recovery procedures to ensure they are functioning correctly and that you can restore your data quickly in case of a disaster.
- Disaster Recovery Plan: Develop a comprehensive disaster recovery plan that outlines the steps to take in case of a major incident, including data recovery, system restoration, and business continuity.
7. Embrace Automation and AI for Enhanced Security
Automation and Artificial Intelligence (AI) are revolutionizing cybersecurity. The "secret" lies in leveraging these technologies to enhance your security posture:
- Security Orchestration, Automation, and Response (SOAR): SOAR platforms automate security tasks, streamlining incident response and improving efficiency.
- AI-powered Threat Detection: AI algorithms can analyze vast amounts of data to identify anomalies and potential threats that might be missed by traditional security systems.
- Automated Vulnerability Management: Automate the process of identifying and remediating vulnerabilities in your systems and applications.
8. Continuous Improvement and Adaptability
The cybersecurity landscape is constantly evolving, with new threats emerging regularly. The "secret" to long-term success is a commitment to continuous improvement and adaptability:
- Regular Security Audits: Conduct regular security audits to assess your organization’s security posture and identify areas for improvement.
- Stay Updated on Emerging Threats: Stay informed about the latest cybersecurity threats and vulnerabilities to proactively address potential risks.
- Embrace a Culture of Security: Foster a culture of security within your organization, where employees are empowered to report security concerns and participate in security initiatives.
Frequently Asked Questions (FAQs):
-
Q: How much should I invest in data security during digital transformation?
- A: The investment in data security should be proportionate to the risk and the value of your data. Consider factors like industry regulations, the sensitivity of your data, and the potential impact of a breach. A comprehensive risk assessment can help determine the appropriate level of investment.
-
Q: What are the key compliance requirements I need to consider?
- A: Compliance requirements vary depending on your industry and location. Familiarize yourself with relevant regulations such as GDPR, CCPA, HIPAA, PCI DSS, etc., and ensure your security practices align with these requirements.
-
Q: How can I ensure my employees are properly trained on security best practices?
- A: Implement a comprehensive security awareness training program that includes regular training sessions, simulated phishing attacks, and clear communication channels for reporting security incidents. Make training engaging and relevant to employees’ roles.
-
Q: How do I choose the right security tools and technologies?
- A: Consider your specific needs and risk profile when selecting security tools. Look for solutions that integrate well with your existing infrastructure and provide comprehensive protection against a range of threats. Consult with security experts to get personalized recommendations.
-
Q: How can I measure the effectiveness of my data security measures?
- A: Track key metrics such as the number of security incidents, the time to resolve incidents, the cost of breaches, and employee awareness levels. Regular security audits and penetration testing can also help assess the effectiveness of your security measures.
-
Q: What should I do if a data breach occurs?
- A: Follow your incident response plan, immediately contain the breach, investigate the cause, notify affected parties as required by law, and take steps to prevent future breaches.
By implementing these strategies and embracing a proactive, holistic approach to security, businesses can navigate the complexities of digital transformation while safeguarding their valuable data. Remember that data security is an ongoing process, requiring continuous monitoring, adaptation, and improvement. The "secret" to success is vigilance, education, and a commitment to protecting your most valuable asset.
Source URL: [Insert a relevant URL from a reputable cybersecurity resource here, e.g., NIST Cybersecurity Framework website]
Closure
Thank you for reading! Stay with us for more insights on “how to secure business data during digital transformations”.
Don’t forget to check back for the latest news and updates on “how to secure business data during digital transformations”!
We’d love to hear your thoughts about “how to secure business data during digital transformations”—leave your comments below!
Stay informed with our next updates on “how to secure business data during digital transformations” and other exciting topics.
.png?width=1758u0026height=1318u0026name=digital%20transformation%20benefits%20(3).png&w=1024&resize=1024,768&ssl=1)