“how to secure APIs for business applications in 2025”
Related Articles
- “top Cybersecurity Certifications For IT Professionals In 2025”
- “best Cloud Storage Options For Secure Business Data 2025”
- “top Data Encryption Tools For Enterprises In 2025”
- “best Practices For Implementing Zero Trust Architecture In Business”
- “ransomware Protection Strategies For Small Businesses 2025”
Introduction
In this article, we dive into “how to secure APIs for business applications in 2025”, giving you a full overview of what’s to come
They power everything from e-commerce platforms and mobile apps to internal systems and IoT devices. However, this reliance on APIs also exposes businesses to significant security risks. In 2025, securing APIs will be more critical than ever, requiring a multifaceted approach that goes beyond basic authentication. This article delves into the "big secret" tips and tricks to ensure your business applications remain safe and secure.
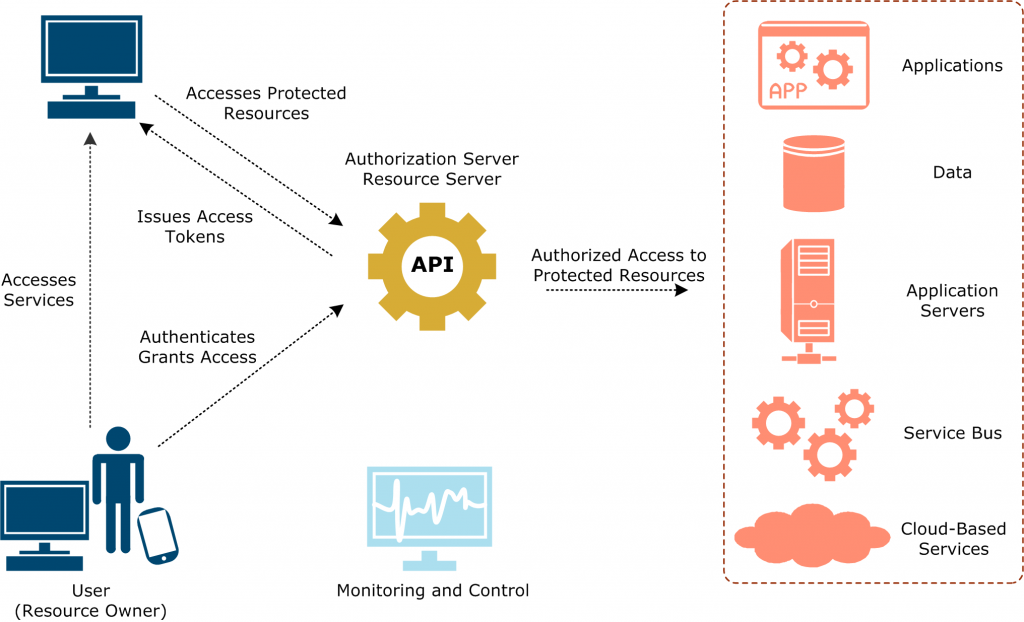
1. Beyond Basic Authentication: Embracing OAuth 2.0 and OpenID Connect
Basic authentication, while simple, is woefully inadequate for modern API security. Credentials are easily intercepted and compromised. OAuth 2.0 and OpenID Connect (OIDC) offer a superior solution. OAuth 2.0 focuses on authorization, allowing applications to access specific resources without needing the user’s password. OIDC builds upon OAuth 2.0 by adding an identity layer, providing verified user information.
Secret Tip: Don’t just implement OAuth 2.0; master it. Understand the different grant types (authorization code, client credentials, etc.) and choose the one best suited for each scenario. Implement robust token management, including refresh tokens with appropriate lifespans and revocation mechanisms. Regularly audit your OAuth configurations to identify and address vulnerabilities. Consider using a dedicated OAuth 2.0 server to simplify management and improve security.
2. API Gateways: Your First Line of Defense
API gateways act as a central point of control and security for all your APIs. They provide several crucial benefits:
- Authentication and Authorization: Gateways enforce access control policies, ensuring only authorized users and applications can access specific APIs.
- Rate Limiting: Prevents denial-of-service (DoS) attacks by limiting the number of requests an application can make within a given timeframe.
- API Key Management: Simplifies the management of API keys, enabling easy revocation and rotation.
- Traffic Monitoring and Logging: Provides valuable insights into API usage, helping identify potential threats and performance bottlenecks.
- Transformation and Routing: Allows for modifications to API requests and responses, facilitating integration with different systems.

Secret Tip: Don’t treat your API gateway as a mere add-on. Integrate it deeply into your security architecture. Configure robust logging and alerting mechanisms to detect suspicious activity. Regularly update the gateway’s firmware and security patches to mitigate vulnerabilities. Consider using a cloud-based API gateway for scalability and enhanced security features.
3. Web Application Firewalls (WAFs) for API Protection
Web Application Firewalls (WAFs) are essential for protecting APIs from common web attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). A WAF sits in front of your APIs, inspecting incoming traffic and blocking malicious requests.
Secret Tip: Don’t rely solely on the default WAF rules. Customize your WAF rules to reflect the specific vulnerabilities and attack vectors relevant to your APIs. Regularly review and update your WAF rules based on emerging threats and security best practices. Consider using a WAF that integrates with your API gateway for seamless protection. Implement a robust logging and monitoring system to track WAF activity and identify potential issues.
4. API Security Testing: The Ongoing Battle
Regular API security testing is crucial for identifying vulnerabilities before attackers do. This involves various techniques, including:
- Static Application Security Testing (SAST): Analyzes your API code for vulnerabilities without executing it.
- Dynamic Application Security Testing (DAST): Tests your running API for vulnerabilities by simulating attacks.
- Interactive Application Security Testing (IAST): Combines SAST and DAST, providing more comprehensive coverage.
- Penetration Testing: Simulates real-world attacks to identify vulnerabilities in your API security posture.
Secret Tip: Don’t limit your testing to just once-a-year exercises. Integrate security testing into your CI/CD pipeline, performing automated tests with every code change. Employ a combination of SAST, DAST, and IAST tools for comprehensive coverage. Engage professional penetration testers regularly to identify vulnerabilities that automated tools may miss. Focus on testing for OWASP API Security Top 10 vulnerabilities.
5. Input Validation and Sanitization: The Foundation of Security
Robust input validation and sanitization are fundamental to API security. Never trust user-supplied data. Always validate and sanitize all inputs before processing them. This prevents various attacks, including SQL injection, XSS, and command injection.
Secret Tip: Don’t just check for data type; validate the data’s content and format. Use parameterized queries or prepared statements to prevent SQL injection. Encode all user-supplied data before displaying it on a webpage to prevent XSS. Implement input length restrictions to prevent buffer overflow attacks. Use a well-defined input validation schema to ensure consistency and completeness.
6. API Documentation and Training: The Human Element
Clear and comprehensive API documentation is crucial for developers using your APIs. It should include details on authentication, authorization, rate limits, error handling, and security best practices. Provide training to developers on secure API development and usage.
Secret Tip: Don’t just create static documentation; make it interactive and easily accessible. Use a dedicated API documentation platform that allows for easy updates and version control. Include examples and code snippets to help developers understand how to use your APIs securely. Conduct regular training sessions for developers on API security best practices and emerging threats. Encourage a security-conscious culture within your organization.
7. Monitoring and Logging: The Eyes and Ears of Your Security
Comprehensive monitoring and logging are essential for detecting and responding to security incidents. Implement logging for all API requests, including authentication attempts, successful requests, and errors. Monitor API usage patterns for anomalies that might indicate attacks.
Secret Tip: Don’t just log basic information; log detailed context, including timestamps, IP addresses, user agents, and request parameters. Use a centralized logging system that allows for easy searching and analysis of logs. Implement real-time monitoring and alerting to detect suspicious activity immediately. Use security information and event management (SIEM) systems to correlate logs from different sources and identify potential threats.
8. Embrace Zero Trust Security Model
The zero-trust security model assumes no implicit trust. Every request, regardless of its origin, is verified before granting access. This approach is particularly crucial for securing APIs, as they are often accessed from various internal and external sources.
Secret Tip: Implement strong authentication and authorization mechanisms at every layer of your API architecture. Use micro-segmentation to isolate your APIs from other systems. Implement continuous monitoring and threat detection to identify and respond to potential threats promptly. Regularly review and update your zero-trust policies to reflect the evolving threat landscape.
Frequently Asked Questions (FAQs)
Q: What are the most common API security vulnerabilities?
A: The OWASP API Security Top 10 provides a comprehensive list of the most common vulnerabilities, including broken object level authorization, excessive data exposure, lack of resource & rate limiting, and insecure design.
Q: How often should I update my API security practices?
A: API security is an ongoing process. Regular updates are crucial, ideally incorporating security testing and vulnerability assessments into your CI/CD pipeline. Stay abreast of emerging threats and best practices.
Q: What is the role of encryption in API security?
A: Encryption is vital for protecting data in transit and at rest. Use HTTPS to encrypt communication between clients and APIs. Encrypt sensitive data stored in databases and other storage systems.
Q: How can I choose the right API security tools?
A: Consider factors such as your budget, the size and complexity of your API landscape, and your specific security needs. Look for tools that integrate well with your existing infrastructure and provide comprehensive features.
Q: What is the cost of neglecting API security?
A: The consequences of neglecting API security can be severe, including data breaches, financial losses, reputational damage, and regulatory fines.
By diligently implementing these strategies, businesses can significantly enhance their API security posture in 2025 and beyond. Remember, API security is a continuous journey, not a destination. Staying informed about emerging threats and adapting your security practices accordingly is crucial for maintaining a strong defense against cyberattacks.
Source URL: https://owasp.org/www-project-top-ten/ (OWASP API Security Top 10)
Closure
Thank you for reading! Stay with us for more insights on “how to secure APIs for business applications in 2025”.
Make sure to follow us for more exciting news and reviews.
Feel free to share your experience with “how to secure APIs for business applications in 2025” in the comment section.
Stay informed with our next updates on “how to secure APIs for business applications in 2025” and other exciting topics.
