“data security trends for financial institutions in 2025”
Related Articles
- “top Cybersecurity Threats To Small Businesses In 2025”
- “best Practices For Implementing Zero Trust Architecture In Business”
- “how AI Is Reshaping Data Security Strategies In 2025”
- “how To Protect Sensitive Business Data From Ransomware”
- “impact Of Quantum Computing On Business Data Encryption”
Introduction
Discover everything you need to know about “data security trends for financial institutions in 2025”
With the increasing reliance on digital transactions and the vast amounts of sensitive personal and financial data held by financial institutions (FIs), data security remains paramount. 2025 presents a landscape significantly different from today, demanding proactive and innovative approaches to safeguarding information. This article delves into the evolving data security trends, offering a glimpse into the "big secret" tips and tricks that FIs will need to master to stay ahead of the curve.
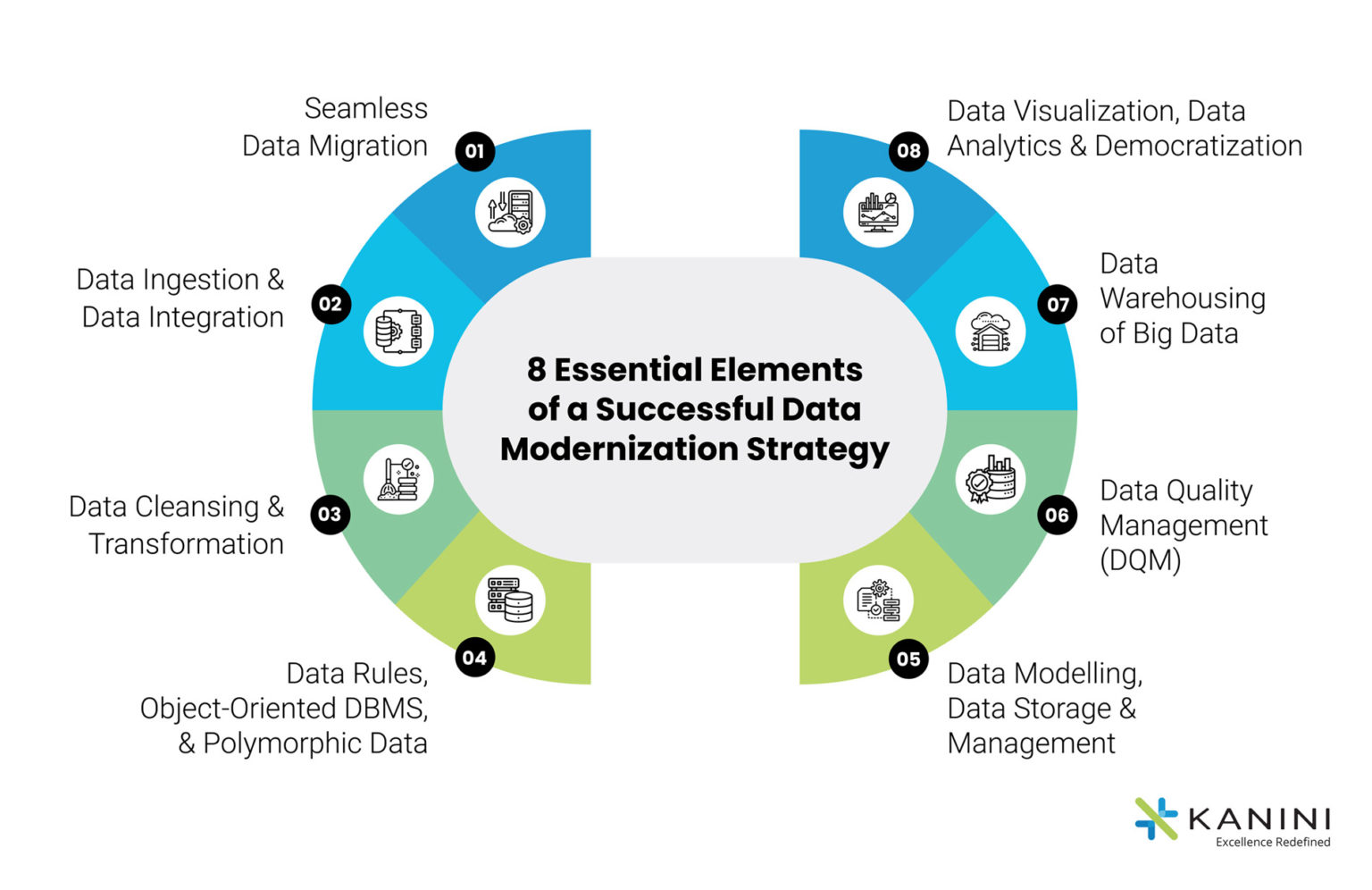
I. The Progression of Data Security Tips and Tricks: From Reactive to Proactive
The evolution of data security in the financial sector has followed a clear trajectory: from reactive measures to proactive, predictive strategies. Initially, security focused on perimeter defenses, firewalls, and anti-virus software. These were essential first steps, but they proved inadequate against sophisticated, targeted attacks.
A. The Era of Reactive Security: This phase was characterized by incident response plans, vulnerability patching after exploits were discovered, and a largely reactive approach to threats. Security breaches were often dealt with after the fact, leading to significant financial losses, reputational damage, and regulatory penalties.
B. The Rise of Proactive Security: The shift towards proactive security involved implementing preventative measures. This included:
- Intrusion Detection and Prevention Systems (IDPS): Moving beyond simple signature-based detection to anomaly-based systems capable of identifying unusual patterns indicative of malicious activity.
- Data Loss Prevention (DLP): Implementing tools and policies to prevent sensitive data from leaving the organization’s control, whether intentionally or accidentally.
- Security Information and Event Management (SIEM): Consolidating security logs from various sources to provide a comprehensive view of the organization’s security posture and facilitate threat detection.
- Regular Security Audits and Penetration Testing: Proactive assessments to identify vulnerabilities before they can be exploited.

C. The Future of Predictive Security: 2025 and beyond will see a further evolution towards predictive security. This involves leveraging advanced analytics, artificial intelligence (AI), and machine learning (ML) to anticipate threats before they occur. This includes:
- AI-powered threat intelligence: Analyzing vast amounts of data from various sources to identify emerging threats and predict potential attacks.
- Behavioral analytics: Monitoring user activity to detect anomalies that may indicate malicious behavior.
- Automated threat response: Systems that automatically respond to threats without human intervention, minimizing the impact of attacks.
- Blockchain technology: For enhanced data integrity and transparency in transactions.
II. Big Secret Tips and Tricks for Data Security in 2025
While many security measures are publicly known, the true "big secret" lies in their effective implementation and integration. It’s not about having the latest technology, but about using it strategically and effectively. Here are some key insights:
A. Embrace Zero Trust Security: The perimeter-based security model is obsolete. Zero trust assumes no implicit trust and verifies every user, device, and application before granting access to resources. This requires robust identity and access management (IAM) systems, multi-factor authentication (MFA), and continuous monitoring. The "secret" is to extend zero trust beyond just network access to encompass all data and applications.
B. Invest in Advanced Threat Detection: Traditional security tools are insufficient to combat sophisticated attacks. FIs need to invest in advanced threat detection technologies that leverage AI and ML to identify subtle anomalies and patterns indicative of malicious activity. The "secret" is not just the technology itself, but the expertise to interpret the data and respond effectively.
C. Prioritize Data Classification and Encryption: Not all data is created equal. FIs need to classify their data based on sensitivity and implement appropriate security controls. Encryption is crucial, both in transit and at rest. The "secret" is to ensure consistent and thorough encryption across all systems and data repositories, including cloud-based services.
D. Focus on Employee Training and Awareness: Human error remains a significant vulnerability. Comprehensive employee training programs are crucial to raise awareness of phishing scams, social engineering attacks, and other threats. The "secret" is to make security training engaging and relevant, emphasizing real-world scenarios and consequences.
E. Develop a Robust Incident Response Plan: Despite the best security measures, breaches can still occur. A well-defined incident response plan is crucial to minimize the impact of an attack. The "secret" is to regularly test and update the plan, ensuring that all stakeholders know their roles and responsibilities.
F. Leverage Blockchain for Enhanced Security: Blockchain technology offers several advantages for data security in the financial sector, including enhanced data integrity, transparency, and immutability. Its application in areas like KYC/AML compliance and secure transaction processing can significantly improve security posture. The "secret" lies in understanding how to integrate blockchain effectively within existing infrastructure without compromising efficiency.
G. Embrace Cloud Security: Many FIs are migrating to the cloud, which presents both opportunities and challenges. Cloud security requires a different approach than on-premises security, with a focus on shared responsibility and robust access controls. The "secret" is to choose reputable cloud providers with strong security credentials and implement appropriate security controls within the cloud environment.
H. Implement Robust API Security: APIs are increasingly used to connect different systems and applications, creating potential vulnerabilities if not properly secured. API security requires strong authentication, authorization, and rate limiting mechanisms. The "secret" lies in implementing comprehensive API security strategies and regularly auditing for vulnerabilities.
III. In-Depth Exploration of the "Big Secret"
The "big secret" to effective data security in 2025 isn’t a single technology or strategy, but rather a holistic approach that integrates people, processes, and technology. It’s about creating a security culture within the organization, where security is not just the responsibility of the IT department, but a shared responsibility across all levels.
This requires:
- A strong security leadership team: Dedicated to driving security initiatives and ensuring that they are aligned with the organization’s overall business objectives.
- A robust security governance framework: Defining roles, responsibilities, and processes for managing security risks.
- Continuous monitoring and improvement: Regularly assessing the effectiveness of security controls and making adjustments as needed.
- Collaboration and information sharing: Working with other FIs, industry groups, and law enforcement agencies to share threat intelligence and best practices.
IV. Conclusion
Data security in 2025 will be more challenging than ever before. FIs need to adopt a proactive and holistic approach, leveraging advanced technologies and a strong security culture. The "big secret" is not about possessing a single magical solution, but about combining multiple strategies, consistently adapting to the evolving threat landscape, and fostering a culture of security throughout the organization. By embracing these tips and tricks, FIs can significantly enhance their resilience against cyberattacks and protect the sensitive data entrusted to them.
V. Frequently Asked Questions (FAQs)
Q1: What is the biggest threat to financial institutions in 2025?
A1: While various threats exist, sophisticated, targeted attacks leveraging AI and ML to bypass traditional security controls will likely pose the greatest challenge. Ransomware attacks and insider threats will also remain significant concerns.
Q2: How much should FIs invest in data security?
A2: There’s no one-size-fits-all answer. Investment should be proportionate to the risk profile of the institution and the sensitivity of the data it handles. A comprehensive risk assessment is essential to determine the appropriate level of investment.
Q3: How can FIs ensure compliance with evolving regulations?
A3: Staying informed about evolving regulations and industry best practices is crucial. FIs should invest in tools and processes to ensure compliance, and regularly conduct audits to identify and address any gaps.
Q4: How can FIs attract and retain cybersecurity talent?
A4: The cybersecurity talent shortage is a significant challenge. FIs need to offer competitive salaries and benefits, provide opportunities for professional development, and create a positive and supportive work environment.
Q5: What is the role of AI in future data security?
A5: AI will play an increasingly important role in threat detection, prevention, and response. AI-powered systems can analyze vast amounts of data to identify anomalies and predict potential attacks, enabling proactive security measures.
Source URL: [Insert a relevant URL here, e.g., a cybersecurity news site or a report from a reputable financial institution.] For example: [https://www.gartner.com/](Replace with a real and relevant URL)
Closure
We hope this article has helped you understand everything about “data security trends for financial institutions in 2025”. Stay tuned for more updates!
Make sure to follow us for more exciting news and reviews.
We’d love to hear your thoughts about “data security trends for financial institutions in 2025″—leave your comments below!
Stay informed with our next updates on “data security trends for financial institutions in 2025” and other exciting topics.
