Businesses can face numerous other legal challenges, including:
Related Articles
- “how To Secure IoT Devices In Corporate Networks”
- “cost Analysis Of Cybersecurity Solutions For SMEs In 2025”
- “how 5G Technology Affects Business Data Security”
- “importance Of Real-time Threat Intelligence In Cybersecurity”
- “how To Train Employees To Prevent Phishing Attacks”
Introduction
Discover everything you need to know about Businesses can face numerous other legal challenges, including:
Businesses can face numerous other legal challenges, including:
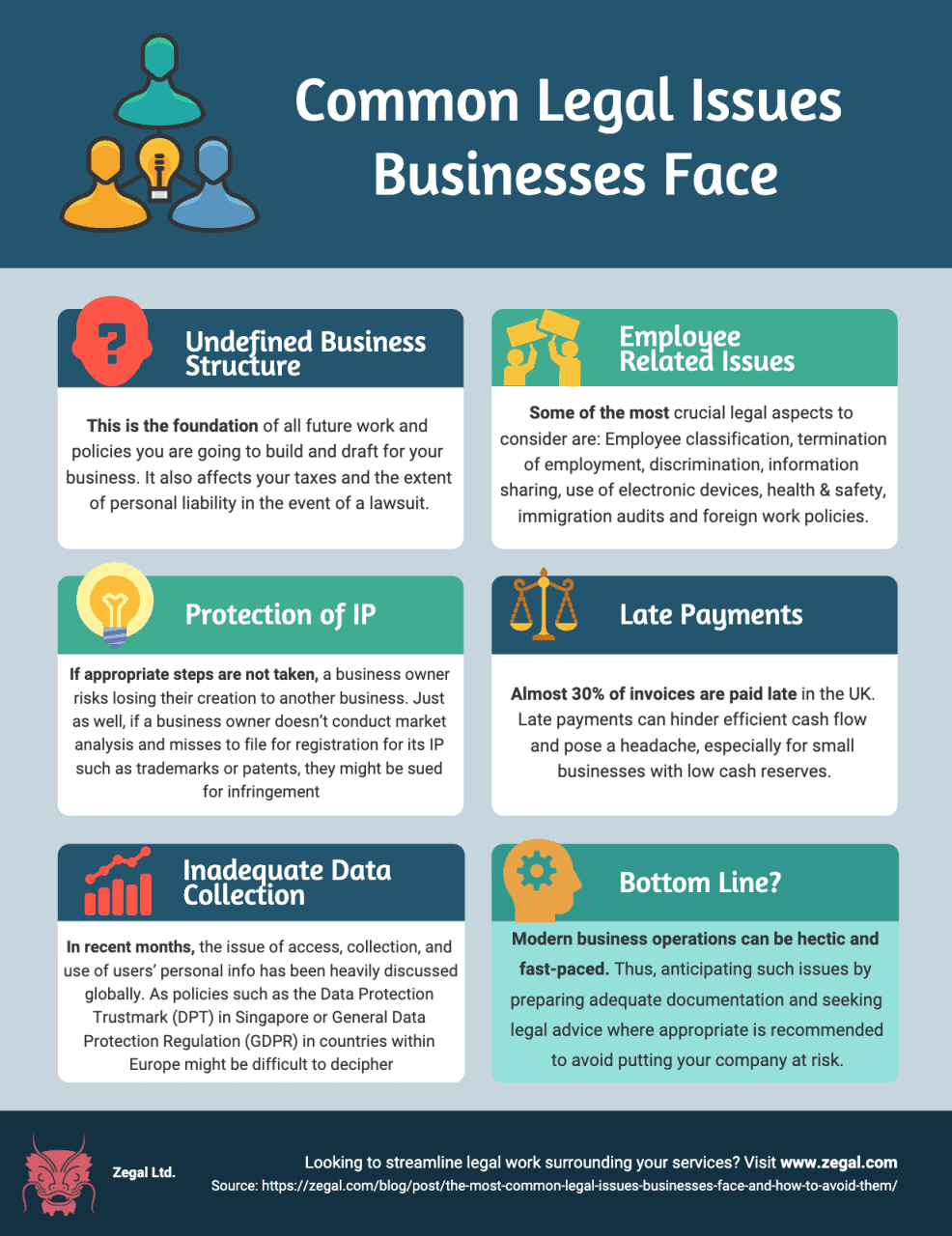
- Consumer Protection Laws: State and federal consumer protection laws, such as the Fair Credit Reporting Act (FCRA) and various state unfair and deceptive trade practices acts, may be invoked if a breach results in identity theft or financial harm to consumers. These laws can lead to significant financial penalties and legal battles.
- Contractual Obligations: Breaches can violate contractual obligations with customers, partners, or employees, leading to breach-of-contract claims. This is particularly relevant when contracts include specific data security clauses or service level agreements (SLAs).
- Regulatory Compliance: Industries like healthcare (HIPAA), finance (GLBA), and education (FERPA) have specific regulations regarding data security and breach response. Non-compliance can lead to hefty fines and sanctions from regulatory bodies.
- Common Law Claims: Businesses may face common law claims such as negligence, breach of fiduciary duty, and invasion of privacy, depending on the circumstances of the breach and the resulting harm to individuals.
Secret Tip: Proactively review all contracts and agreements to identify data security clauses and ensure your practices align with those obligations. Conduct regular risk assessments to identify vulnerabilities and implement appropriate safeguards to minimize legal exposure across all potential areas of liability.
3. The Importance of a Robust Incident Response Plan
A well-defined and tested incident response plan is not just a "best practice"; it’s a legal necessity. A reactive approach to a data breach significantly increases the risk of legal repercussions. A proactive plan should include:
- Data Inventory and Classification: Understanding what data you hold, where it’s stored, and its sensitivity is paramount. This allows for a swift and targeted response in the event of a breach.
- Incident Detection and Response Team: Establish a dedicated team with clear roles and responsibilities to handle breach investigations and notifications.
- Forensic Investigation: Engage experienced forensic experts to investigate the breach, determine its scope, and identify the root cause. This evidence is crucial in defending against lawsuits and demonstrating compliance with legal requirements.
- Notification Procedures: Develop clear procedures for notifying affected individuals, regulatory bodies, and law enforcement, adhering to all applicable state and federal laws.
- Public Relations Strategy: A well-crafted communication plan can mitigate reputational damage. This includes preparing pre-written statements and designating a spokesperson to manage media inquiries.

Secret Tip: Regularly test your incident response plan through simulated breaches to identify weaknesses and ensure its effectiveness. Document all actions taken during the response, preserving crucial evidence for potential legal proceedings.
4. Insurance as a Critical Component of Data Breach Preparedness
Cybersecurity insurance is no longer a luxury; it’s a vital component of a comprehensive risk management strategy. A well-structured policy can cover the costs associated with:
- Notification: Costs related to notifying affected individuals and regulatory bodies.
- Forensic Investigation: Expenses for hiring forensic experts to investigate the breach.
- Legal Fees: Costs associated with defending against lawsuits and regulatory investigations.
- Credit Monitoring and Identity Restoration Services: Providing affected individuals with credit monitoring and identity restoration services.
- Public Relations: Expenses related to managing the public relations fallout from the breach.
Secret Tip: Carefully review different insurance policies to ensure they adequately cover your specific needs and the potential scope of a data breach in your industry. Don’t just focus on the premium; consider the coverage limits and the insurer’s reputation for handling data breach claims.
5. Proactive Measures: Prevention is Better Than Cure
While responding to a breach is crucial, preventing them in the first place is paramount. Proactive measures include:
- Regular Security Audits and Penetration Testing: Regularly assess your security infrastructure for vulnerabilities and conduct penetration testing to identify weaknesses.
- Employee Training: Educate employees on cybersecurity best practices, including phishing awareness and password management.
- Multi-Factor Authentication (MFA): Implement MFA to enhance the security of your systems and access controls.
- Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Access Control: Implement robust access control measures to limit access to sensitive data to only authorized personnel.
Secret Tip: Don’t rely solely on technical solutions. A strong security culture within your organization, where employees are actively involved in security awareness, is just as important as technical safeguards.
6. Document Everything: The Power of Evidence
Meticulous documentation is crucial in mitigating legal risks. Maintain comprehensive records of:
- Security Policies and Procedures: Document your security policies, procedures, and training programs.
- Risk Assessments: Regularly conduct and document risk assessments to identify and mitigate vulnerabilities.
- Incident Response Activities: Maintain detailed records of all activities undertaken during a data breach response.
- Vendor Management: Document your contracts with third-party vendors and their security practices.
Secret Tip: Establish a centralized system for storing and managing all security-related documentation. This ensures easy access to crucial information during an investigation or legal proceedings.
7. Engaging Legal Counsel: Seeking Expert Guidance
Engaging experienced legal counsel specializing in data breach response is essential. A lawyer can provide guidance on:
- Compliance with Notification Laws: Ensuring compliance with all applicable state and federal notification laws.
- Negotiating with Regulatory Bodies: Navigating interactions with regulatory bodies like the FTC or state attorneys general.
- Defending Against Lawsuits: Representing your business in lawsuits arising from a data breach.
- Developing Mitigation Strategies: Developing strategies to mitigate legal risks and minimize potential damages.
Secret Tip: Establish a relationship with legal counsel before a breach occurs. This allows for proactive planning and ensures you have access to expert advice when you need it most.
8. The Ongoing Evolution of Data Privacy Laws
The legal landscape surrounding data breaches is constantly evolving. Stay informed about new laws, regulations, and court decisions that may impact your business. Subscribe to legal updates, attend industry conferences, and consult with legal experts to ensure your practices remain compliant.
Secret Tip: Monitor proposed legislation and regulatory changes at both the federal and state levels. Proactive adaptation to evolving legal requirements is crucial for minimizing long-term legal risk.
Frequently Asked Questions (FAQs)
Q: What is the average cost of a data breach?
A: The cost varies significantly depending on factors such as the size of the breach, the type of data compromised, and the industry. However, the average cost can run into millions of dollars, encompassing legal fees, forensic investigations, notification costs, and potential fines.
Q: Do I need to notify every individual affected by a data breach?
A: This depends on the specific state laws applicable to your business and the type of data compromised. Generally, notification is required if personal information meeting a specific definition under state law is involved.
Q: What happens if I fail to comply with data breach notification laws?
A: Failure to comply can result in significant fines, class-action lawsuits, reputational damage, and even criminal charges in some cases.
Q: Can my business be held liable for a data breach caused by a third-party vendor?
A: Yes, businesses can be held liable for breaches caused by third-party vendors, especially if they failed to adequately vet the vendor or implement appropriate security measures. Strong vendor contracts with robust security clauses are crucial.
Q: How can I improve my organization’s cybersecurity posture?
A: Implementing a multi-layered approach to security, including technical safeguards, employee training, robust incident response planning, and regular security assessments, is crucial.
This article provides a comprehensive overview of the legal implications of data breaches for businesses in the USA. However, it’s crucial to remember that this information is for educational purposes only and does not constitute legal advice. Consult with legal and cybersecurity professionals to address your specific circumstances and ensure compliance with all applicable laws and regulations.
Source URL: [Insert a relevant URL here, such as a link to a reputable law firm specializing in data breach litigation or a government website providing information on data breach laws. For example: https://www.ftc.gov/business-guidance/data-security ]
Closure
Thank you for reading! Stay with us for more insights on Businesses can face numerous other legal challenges, including:.
Don’t forget to check back for the latest news and updates on Businesses can face numerous other legal challenges, including:!
Feel free to share your experience with Businesses can face numerous other legal challenges, including: in the comment section.
Stay informed with our next updates on Businesses can face numerous other legal challenges, including: and other exciting topics.
