Best practices for securing remote work data access
Related Articles
- “how To Train Employees To Prevent Phishing Attacks”
- “emerging Cybersecurity Threats For Supply Chain Operations In 2025”
- Zero-trust Security Models For SMBs In 2025
- “ransomware Recovery Strategies For Enterprises In 2025”
- “benefits Of Using Multi-factor Authentication For Businesses”
Introduction
Discover everything you need to know about Best practices for securing remote work data access
However, this shift also presents significant challenges to data security. Securing data access for remote employees requires a multi-layered approach, going beyond simple VPNs and password policies. This article delves into the often-overlooked aspects of remote work security, revealing "big secret" tips and tricks to bolster your organization’s defenses.
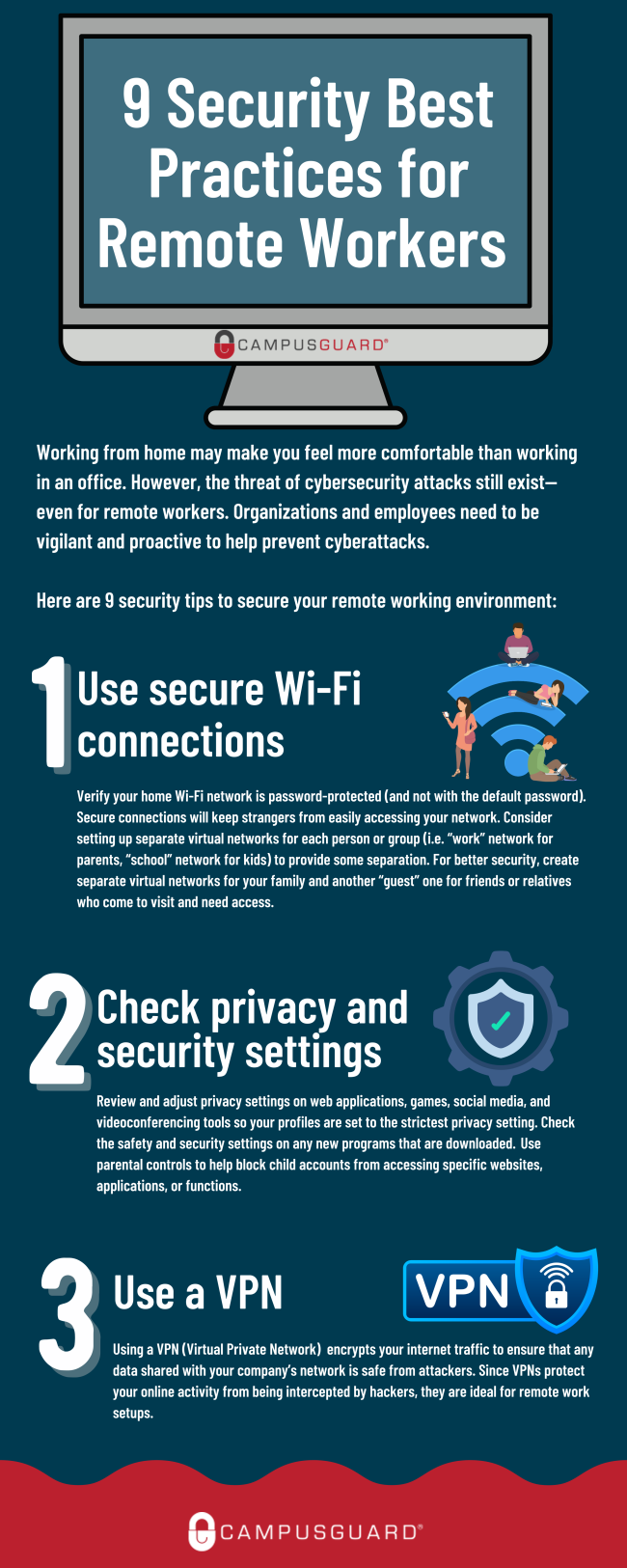
1. Beyond the VPN: Advanced Network Security Strategies
While a Virtual Private Network (VPN) is a crucial first step, it’s not a silver bullet. Many organizations rely solely on VPNs, leaving significant vulnerabilities exposed. To truly secure remote access, consider these advanced strategies:
-
Zero Trust Network Access (ZTNA): ZTNA moves beyond the "trust but verify" model inherent in VPNs. It assumes no implicit trust, verifying every user and device before granting access to specific resources, regardless of network location. This granular control significantly reduces the attack surface.
-
Microsegmentation: Divide your network into smaller, isolated segments. This limits the impact of a breach. If one segment is compromised, the attacker won’t have immediate access to the entire network. This is particularly important for sensitive data like financial records or customer information.

Multi-Factor Authentication (MFA) Beyond the Basics: While MFA is essential, don’t stop at the standard SMS or email codes. Implement stronger authentication methods like hardware security keys (like YubiKeys) or biometric authentication. These are significantly harder to compromise than simpler methods.
-
Regular Network Penetration Testing: Don’t just rely on your own internal security team. Engage external penetration testing experts to simulate real-world attacks and identify vulnerabilities you might have missed. This proactive approach is far more cost-effective than reacting to a data breach.
2. Device Security: Hardening Endpoints for Remote Access
Securing the network is only half the battle. The devices used to access that network – laptops, tablets, smartphones – must also be hardened against threats.
-
Endpoint Detection and Response (EDR): EDR solutions go beyond traditional antivirus software. They monitor endpoint activity for malicious behavior, providing real-time threat detection and response capabilities. This is crucial for identifying and neutralizing threats before they can cause significant damage.
-
Mobile Device Management (MDM): For organizations allowing access from personal devices (BYOD), MDM is paramount. MDM solutions allow you to enforce security policies on employee devices, such as password complexity requirements, data encryption, and remote wiping capabilities.
-
Regular Software Updates and Patching: Keeping all software – operating systems, applications, and firmware – up-to-date with the latest security patches is critical. Automated patching systems can significantly simplify this process and reduce the risk of vulnerabilities being exploited.
-
Data Loss Prevention (DLP): DLP tools monitor data movement to prevent sensitive information from leaving the organization’s control. They can identify and block attempts to copy, print, or email confidential data to unauthorized locations.
3. Data Encryption: The Cornerstone of Remote Work Security
Encryption is the foundation of any robust data security strategy. It protects data both in transit and at rest.
-
End-to-End Encryption: For sensitive communications, utilize end-to-end encryption tools. This ensures that only the sender and recipient can access the data, even if the communication is intercepted.
-
Data Encryption at Rest: Encrypt all data stored on servers, laptops, and other devices. This protects data even if the device is lost or stolen. Utilize strong encryption algorithms like AES-256.
-
Secure Cloud Storage: If using cloud storage, ensure the provider offers robust security features, including encryption at rest and in transit, access controls, and regular security audits.
4. Access Control and Privilege Management: The Principle of Least Privilege
Granting users only the access they need to perform their jobs is crucial. This principle of least privilege minimizes the damage caused by a compromised account.
-
Role-Based Access Control (RBAC): RBAC assigns permissions based on roles within the organization. This simplifies access management and reduces the risk of over-privileged accounts.
-
Just-in-Time Access: Grant temporary access only when needed, rather than providing permanent access. This reduces the window of vulnerability.
-
Regular Access Reviews: Periodically review user access rights to ensure they still align with their roles and responsibilities. Remove access for employees who have left the company or changed roles.
5. Security Awareness Training: Empowering Employees as Your First Line of Defense
Employees are often the weakest link in the security chain. Comprehensive security awareness training is essential to empower them to protect the organization’s data.
-
Phishing Simulations: Regularly conduct phishing simulations to test employee awareness and identify vulnerabilities. This helps to train employees to identify and report suspicious emails and websites.
-
Security Best Practices Training: Educate employees on security best practices, such as strong password creation, recognizing social engineering tactics, and reporting security incidents.
-
Continuous Learning: Security threats are constantly evolving. Provide ongoing security awareness training to keep employees updated on the latest threats and best practices.
6. Incident Response Planning: Preparing for the Inevitable
Despite the best security measures, breaches can still occur. A well-defined incident response plan is crucial for minimizing the impact of a security incident.
-
Incident Response Team: Establish a dedicated incident response team responsible for handling security incidents. This team should have clear roles and responsibilities.
-
Incident Response Procedures: Develop detailed procedures for handling security incidents, including steps for containment, eradication, recovery, and post-incident analysis.
-
Regular Drills and Simulations: Conduct regular drills and simulations to test the incident response plan and identify areas for improvement. This ensures the team is prepared to respond effectively in a real-world scenario.
7. Monitoring and Logging: The Eyes and Ears of Your Security Posture
Real-time monitoring and comprehensive logging are essential for detecting and responding to threats.
-
Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events. They can identify suspicious activity and alert security personnel to potential threats.
-
Intrusion Detection and Prevention Systems (IDPS): IDPS systems monitor network traffic for malicious activity, blocking or alerting on suspicious patterns.
-
Regular Log Analysis: Regularly analyze security logs to identify trends and potential threats. This proactive approach can help to prevent future incidents.
8. Compliance and Regulations: Meeting Legal and Industry Standards
Depending on your industry and location, you may be subject to specific data protection regulations, such as GDPR, CCPA, HIPAA, or others. Ensure your remote work security practices comply with all applicable regulations. Regular audits and assessments can help to maintain compliance.
Frequently Asked Questions (FAQs)
Q: What is the best VPN for remote work?
A: There’s no single "best" VPN. The ideal VPN depends on your specific needs and security requirements. Consider factors like security features, performance, ease of use, and compliance certifications. Research reputable providers and compare their offerings.
Q: How can I prevent data breaches caused by employee negligence?
A: A multi-pronged approach is crucial: strong security awareness training, robust access control policies, and regular security audits are all essential. Implementing DLP tools can also help prevent accidental data leakage.
Q: Is BYOD (Bring Your Own Device) secure?
A: BYOD can be secure if properly managed. Implementing an MDM solution is critical to enforce security policies on employee devices and protect company data. Clear policies and employee training are also vital.
Q: What should I do if I suspect a data breach?
A: Immediately follow your organization’s incident response plan. Isolate affected systems, gather evidence, and notify the appropriate authorities (if required). Engage your incident response team and legal counsel.
Q: How often should I update my security software?
A: Security software should be updated as soon as patches are released. Automated patching systems can greatly simplify this process. Regularly check for updates and ensure all systems are up-to-date.
Securing remote work data access is an ongoing process, requiring continuous vigilance and adaptation. By implementing these best practices and staying informed about emerging threats, organizations can significantly reduce their risk and protect their valuable data.
[Source URL: (Insert a relevant URL here, e.g., a cybersecurity company’s best practices page or a government resource on data security)]
Closure
Thank you for reading! Stay with us for more insights on Best practices for securing remote work data access.
Make sure to follow us for more exciting news and reviews.
Feel free to share your experience with Best practices for securing remote work data access in the comment section.
Stay informed with our next updates on Best practices for securing remote work data access and other exciting topics.
